
Get going in minutes with no SnowSQL, no contracts, no cost, no consultants and... really, no hassle, with our SaaS cloud-based platform.

Sign up here or connect to your Enterprise Edition Snowflake account via Snowflake Partner Connect to get started.

Data Tokenization and Format Preserving Encryption

Dynamic Data Masking and Data Access Governance

Database Activity Monitoring

Open-Source Data Catalog and ETL Integrations

Data Discovery and Classification


Secure your data using ALTR's Format Preserving Encryption offering. Built off the industry leading FF3_1 algorithm, this method adds an additional layer of at-rest security, while maintaining data usability through determinism alongside length and format preservation.

Maximize protection, and reduce compliance burden using ALTR's SaaS Tokenization Vault. Ideal for securing highly sensitive data, such as PHI or PCI, without sacrificing performance.

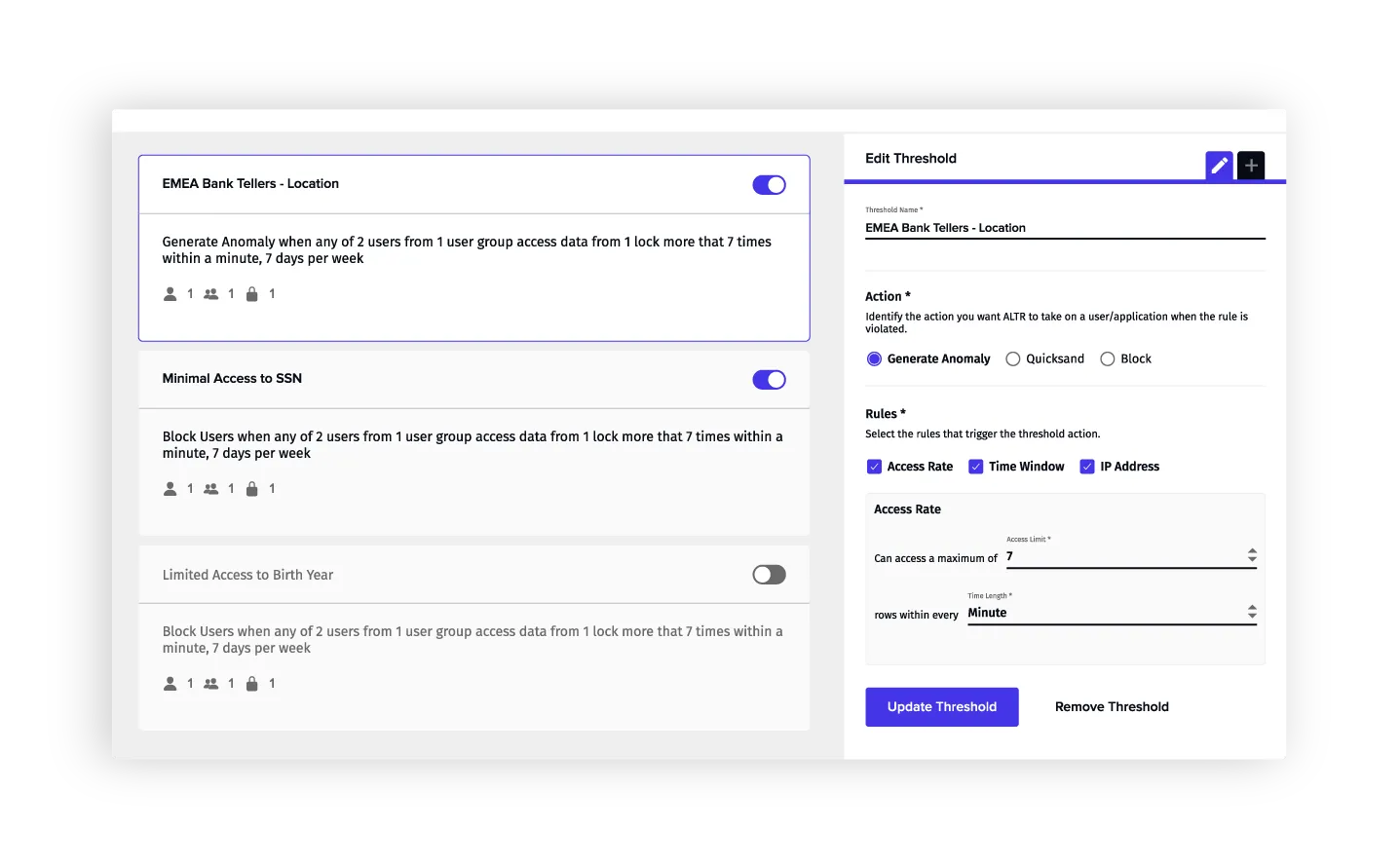
Monitor all access to sensitive data controlled by ALTR with rich query logs. Alert security teams when data access surpasses normal thresholds.

Identify what data is sensitive through built-in data classification or your own classification method. Use classification insights to automatically control data access.

Easily identify how much data specific users are accessing. Easily analyze access trends over time to ensure policy is properly configured.

Protect sensitive data with column-based and row-based access policies and dynamic data masking. Scale policy creation with attribute-based and tag-based access control.