Since Salesforce launched at the end of last century, the cloud application boom has been unstoppable. Along with that has come another boom: cloud-hosted data. The rise of digital transformation, as well as other trends like mobile and IoT, has led to a massive increase in the amount of data created. In fact, 64.2 Zettabytes of data was created or replicated in 2020 according to IDC. That’s 10^21 bytes of data!
Now, all that data represents a rich resource of knowledge to business – from where consumers visit online to how companies make purchases. And the best way to get value from it is to consolidate the multitude of data points and put machine learning, AI or Big Data tools on top of it to connect the dots. This data analysis can either be done in an on-premises data warehouse or in the cloud. Doing it in the cloud delivers some compelling benefits including virtually unlimited scalability with no costs for infrastructure investment and lower ongoing maintenance. The attractiveness of the cloud data warehouse model is one of the reasons Snowflake debuted with the biggest software IPO ever in 2020.
But consolidating all this data, especially sensitive data, into the cloud creates a serious challenge for Chief Information Security Officers (CISOs): how can they be 100% responsible for data security when they have 0% control over the infrastructure where it’s stored?
The cloud data accountability/control mismatch
CISOs and their security teams had their roles nailed down: secure the datacenters with firewalls, stop employees from clicking on phishing emails or accessing malware infected websites, and protect the company perimeter from hackers and outside threats. These were tactics meant to deliver specific and important end results: keep the network safe and protect company data. Forrester Research calls this “Zero-Trust”, but it’s a perimeter defense mechanism that does not apply to the “perimeter-less” cloud.
But today, a Chief Marketing Officer (CMO) may look at the rich data streams moving throughout the company, generated by 15 or 20 different applications, with hundreds of data points about customers and prospects, and make the argument that if only that data were combined, it could deliver a minutely-detailed composite of individual users and buyers – and marketing could raise revenue by 8%.
The CMO gets the go ahead to move that data to Snowflake, but where does that leave the CISO? Suddenly, the data is in an environment he or she doesn’t control. Increasingly the business project is taking a much higher priority and security is trying to catch up. The CISO is still responsible for securing data that’s been moved outside the nice, cozy, protected perimeter the security team has spent years perfecting. If there’s a data breach, they’re still on the hook, they could still get fired, but how can they stop that if they don’t control the space?
The CISO is still responsible, even when data leaves home
Think of it like a parent who lets their children stay overnight at a friend’s house. The parent is still responsible for the child’s safety, so shouldn’t they ask the friend’s parents some questions? Find out about the culture of the home? Who the parents’ friends are? What kind of rules they impose? The parent doesn’t stop being responsible or stop worrying once their child leaves the home. And they certainly don’t lock their children up at home in order to “keep them safe” – that’s not reasonable.
Some CISOs and Chief Risk Officers try to maintain control by placing stringent rules around how the data can be stored and used in cloud data warehouses. I’m aware of one that requires sensitive data to be stored on Snowflake only when encrypted or tokenized. In order to be used or operated on, it has to be moved into a secure on-prem environment the CISO controls, de-crypted/de-tokenized, utilized, then encrypted or tokenized before being transferred back to Snowflake.
It may be secure, but it’s like making your child come home to ask permission before playing a game or having a snack at the sleepover. It’s really clunky and slows things down. Some security execs are jumping through a lot of hoops to overcome this accountability and control mismatch.
Others are just abdicating control and trusting cloud data warehouse providers. This leaves a hole in security: these providers have taken over responsibility for maintaining the infrastructure, the perimeter, the physical space, but they’re not taking on the responsibility of user identity and access or the data itself – that still resides with the company, especially the CISO. To be clear, Snowflake is very secure, but the more successful they become the more a target they are for bad actors and especially nations-states.
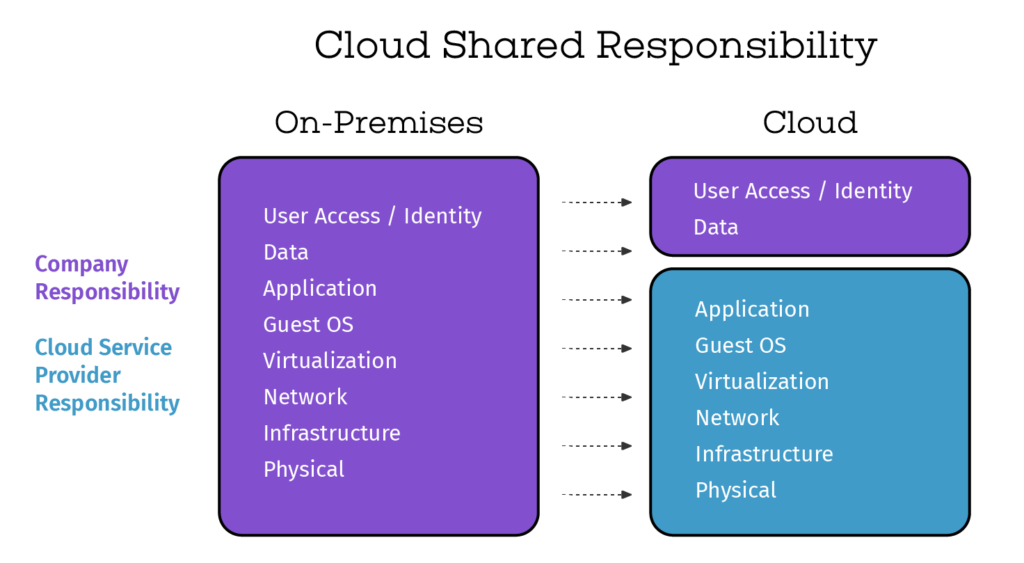
Moving beyond perimeter-centric to data-centric security
This shift to the cloud really requires a shift in the security mindset: from perimeter-centric to data-centric security. It means CISOs and security teams need to stop thinking about hardware, datacenters, perimeters and start focusing on the end goal: protecting the data itself. They need to embrace data governance and security policies around data. They need to understand who should have access to the data, understand how data is used, and place controls and protections around data access. They should look for a combined data governance and security solution that delivers complete data control and protection.
Because bad actors don’t care who’s responsible—they’re going where the data is and taking advantage of any holes they find. The 2021 Verizon Data Breach Investigations Report (DBIR) showed this clearly: this year 73 percent of the cybersecurity incidents involved external cloud assets. This is a complete flip-flop from 2019, when cloud assets were only involved in 27 percent of breaches.
Regulators also don’t care where data is when it comes to responsibility for keeping it safe: it’s on the company who collects it. Larger companies in more regulated industries face very large, really punitive fines if there’s a data leak—which can lead to severe consequences for the business…and the CISOs responsible.
If CISOs want to not only catch up to but get ahead of business priorities, bad actors, and regulatory requirements, they need to focus on controlling, protecting and minimizing risk to data—wherever it is.



