One data security platform for data protection and access control
Our user-friendly SaaS platform makes it easy for data and infosec teams of all sizes to secure regulated data immediately.
















One powerful platform for your
data team

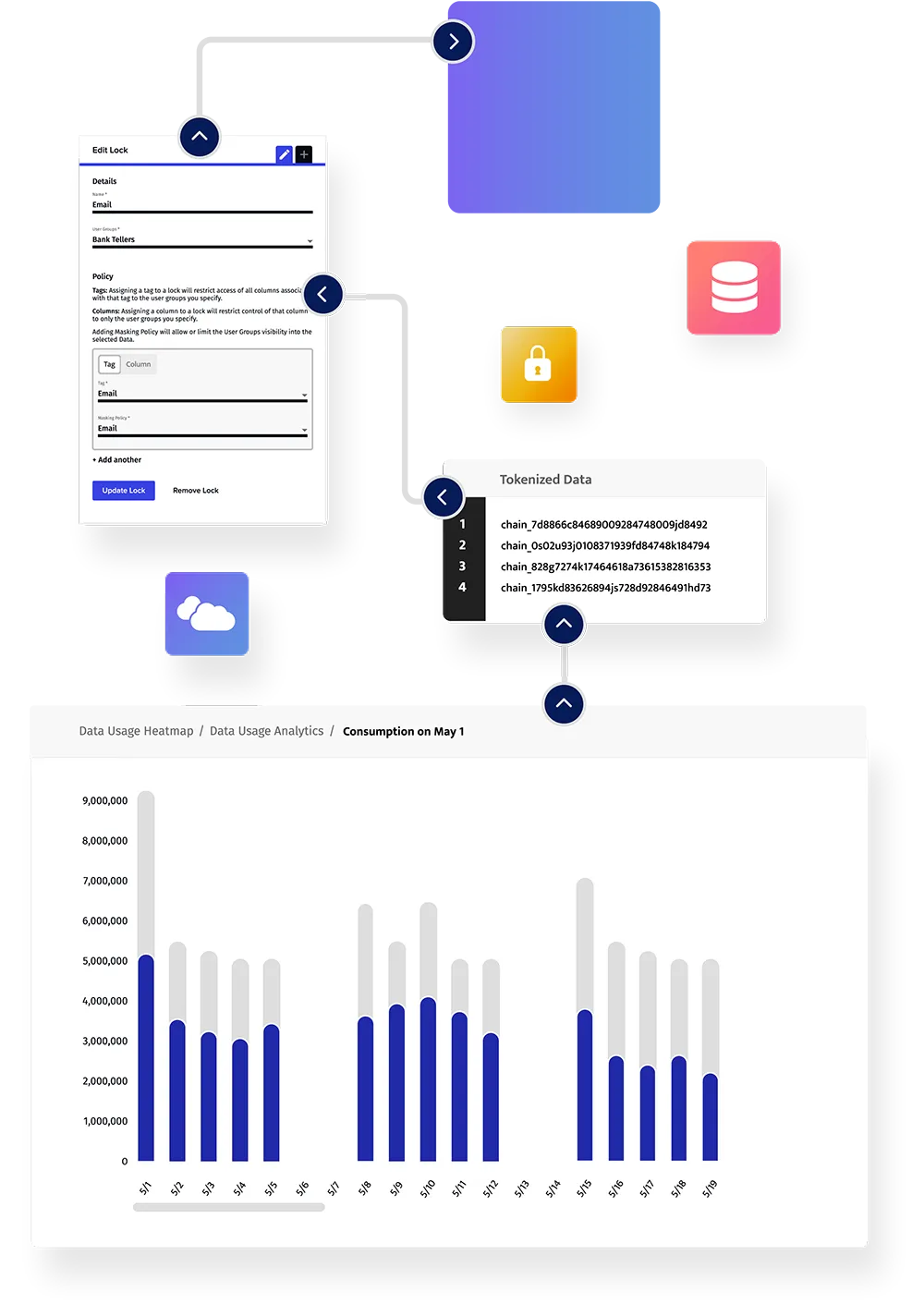
Dynamic Data Masking

Data Activity Monitoring

Data Classification

Tokenization

Open Source Integrations

Format Preserving Encryption
Simplified data security and data access governance
Data teams get real-time access to sensitive data without risk while security teams gain full visibility over sensitive data. All data functions are fully aligned.
Non-technical users can implement policy and simplify ownership so data can remain streamlined and automated.
Protection for at rest, in motion, and in use data. Remove the risk of access threats by extending governance and security upstream and to the left.
Data teams
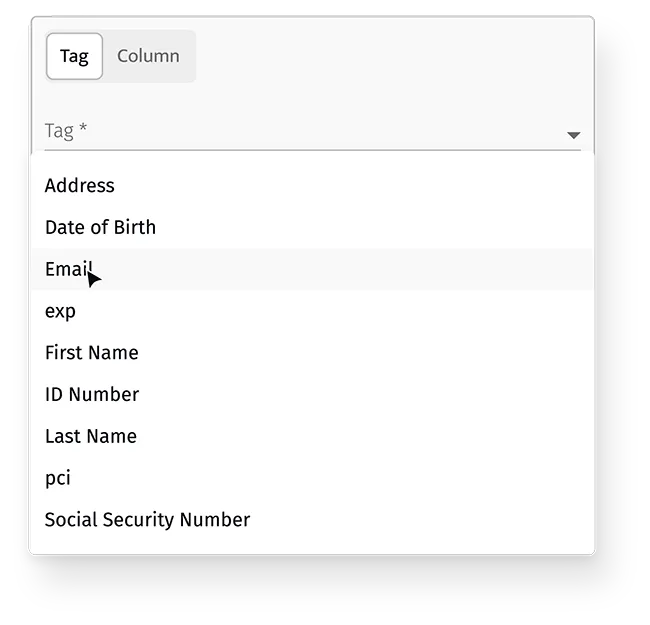
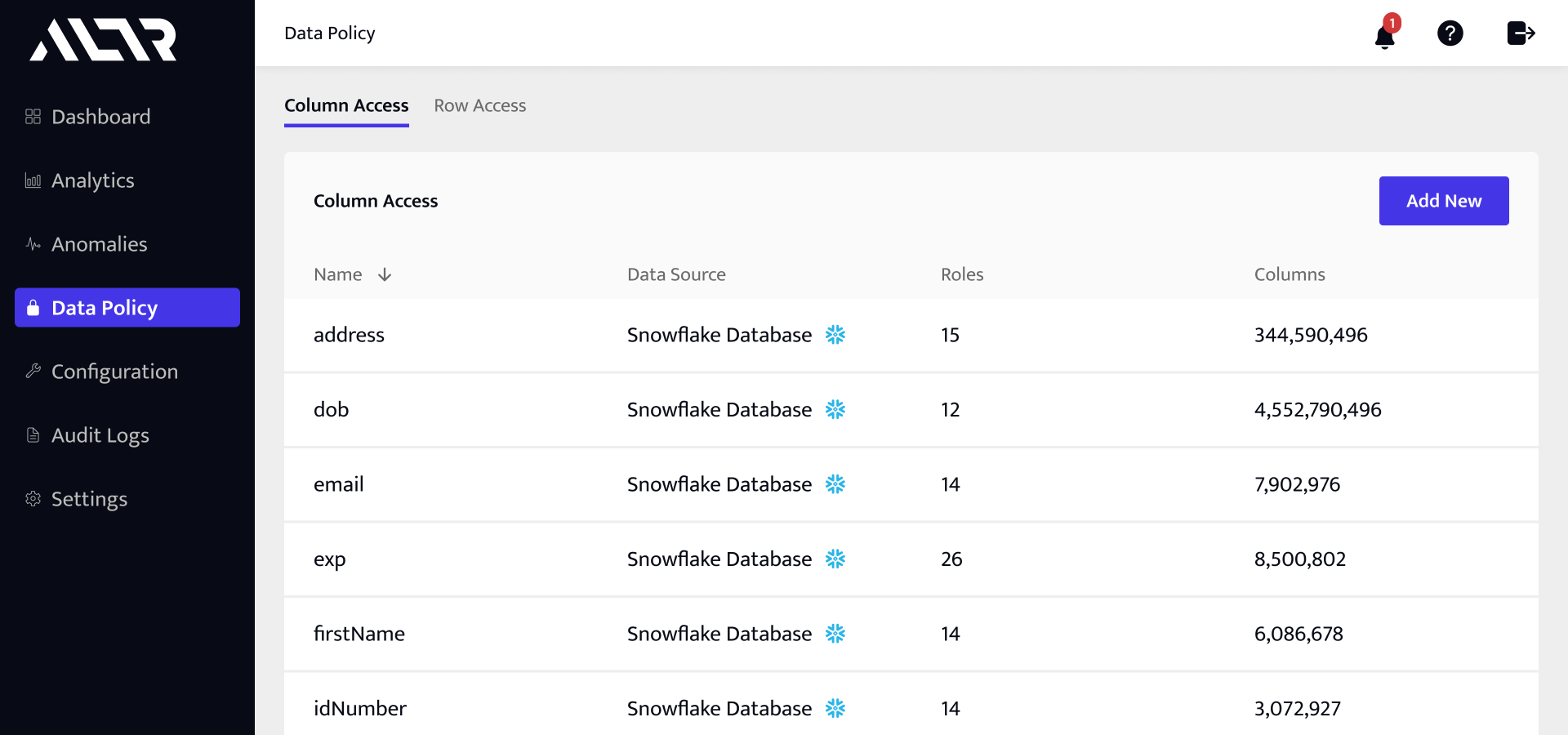
Quickly identify and protect sensitive data with our automated classification tools and govern high-risk values to meet compliance needs.
Set up automated access controls with our dynamic data masking capabilities to ensure proper access to credentialed users.

Infosec teams
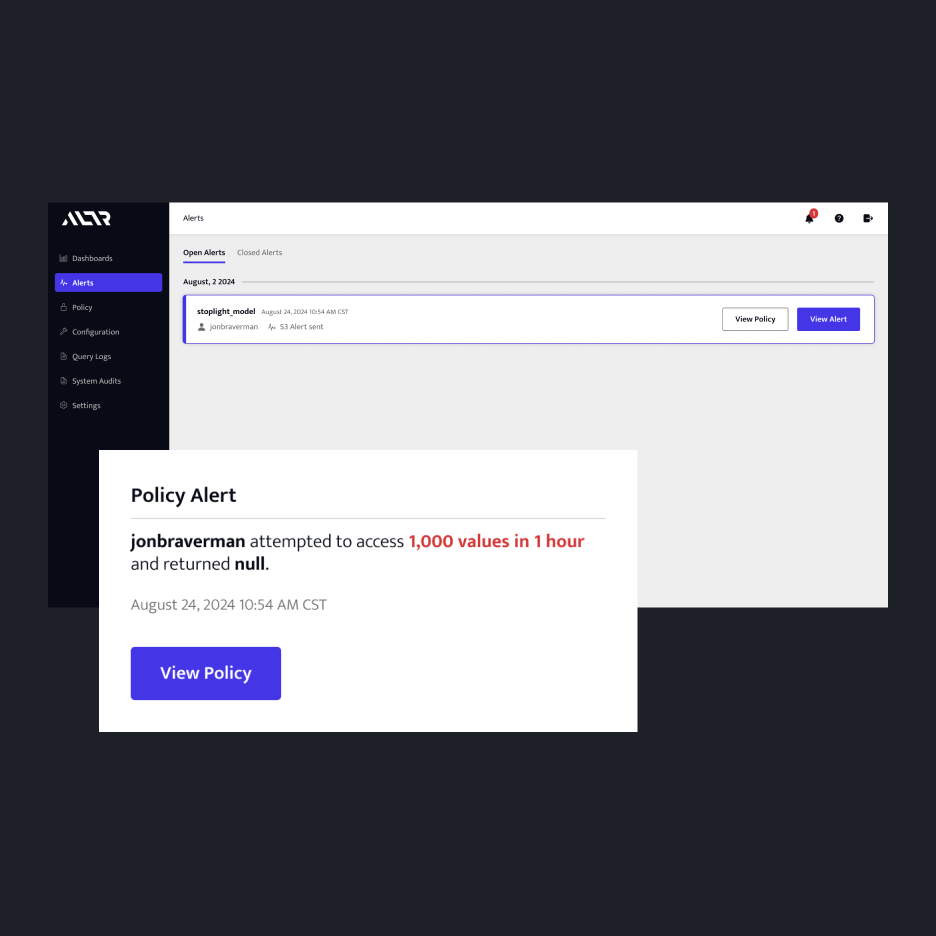
Achieve real-time observability over how sensitive data is consumed in the cloud with active alerts for unauthorized requests.

Secure data from source to cloud with automated data access governance so sensitive data is never at risk.

6X
more protected data in your database
35 seconds
average time to create a policy
40%
fewer policies to manage

Blog


.png)